Secure Access Service Edge (SASE) –The Ultimate Guide
So, you have seen the SASE (pronounced Sassy) term floating around. It stands for Secure Access Service Edge.
According to a few industry surveys, there is still a lot of confusion about what it means.
People have confused it with SD-WAN and even though the two were in competition.
So, let’s break down this latest marketing buzzword for you.
Table of Contents
What is Secure Access Service Edge (SASE)?
SASE is a convergence of many security and networking technologies. The combination of these creates a unified cloud-delivered service to handle both security and connectivity at every network edge.
This image demonstrates many of the technologies that you might find in a SASE deployment model.
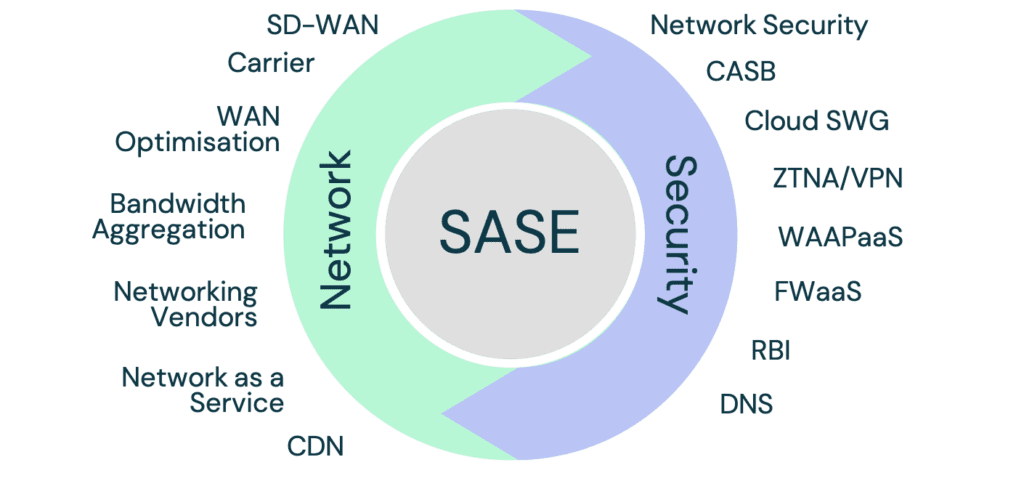
What it is not
SASE is not a specific technology, solution, or feature.
Therefore, it cannot compete with any of the solutions it contains.
So, if you read an article saying that SASE will replace any of these products, think again.
They can all be a part of the fabric of a SASE deployment.
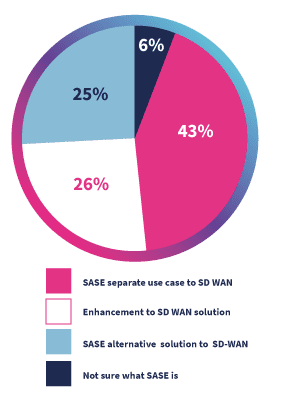
In this chart from Accelerate below, you can see there is still a lot of confusion.
While this may have been due to how they asked the question, the most accurate answer here is that it is an “enhancement to an SD-WAN solution” as it is an option for securing SD-WAN networks.
SASE definition
The combining of security and networking into one unified cloud service.
SASE is a response to the growing complexity of security and network technologies.
Both industries have needed to create systems capable of shifting from centralised corporate data centres to dispersed cloud locations.
Both the shift to a decentralised and mobile workforce, and increasing reliance on cloud-hosted applications created the demand for a distributed network.
Adding the levels of security to support the distributed network required tighter integration with cloud networking – which in turn created the idea of SASE.
SASE sees both network and security tools deployed through the cloud.
When these combine with central management and modular deployment options, SASE can help companies build a more responsive and secure network.
While the main drivers for SASE is the growth of the distributed workforce, the other is the expanding network edge.
What is the network edge?
A network edge is the point closest to the user where the internet or local network ends.
In the early days of networks, the definition of the edge only included network connectivity devices like routers.
With the arrival of more complex devices like smartphones with their own connectivity, the network edge is less defined.
Now, an edge device can be any that connects to the internet or enables an internet connection.
This includes routers, Wi-Fi hubs, smartphones, PCs, and IoT devices.
5G, and the level of services it enables, will continue to expand this to include more and more types of devices.
SASE Components
SASE includes the following technologies:
1. Firewall (FW)
2. Route and Path Selection
3. Quality of Service control
4. VPN/Zero Trust Network Access (ZTNA)
5. Threat Prevention/Detection
6. Geo Restrictions
7. Cloud App Discovery
8. Cost Optimization
9. User and Entity Behaviour and Analytics (UEBA)/Fraud
10. DNS Protection
11. Sensitive Data Discovery
12. Obfuscation/Privacy
13. Web Application Firewall (WAF)/Web Application and API Protection (WAAP)
14. Bandwidth Optimization and Deduplication
15. Remote Browser Isolation
16. Wi-Fi Protection
17. SaaS Acceleration
18. Secure Web Gateway (SWG)
19. Traffic Shaping
20. Data Loss Prevention (DLP)
21. Latency Reduction
22. Software Defined Perimeter
23. Caching/Content Demand Network (CDN)
24. Network Encryption/Decryption
25. Path Resilience/Redundancy
26. Cloud Access Security Broker (CASB)
It’s important to note that while these products are included in the definition of what SASE can include, each solution is different.
Need a deeper dive into these technologies and how they relate to SASE? Find out more in the State of SASE Networking: 2021 Report.
What is the difference between SASE Vendors?
Solutions in the SASE space will vary based on the legacy of the company that is building the service.
In 2020, Versa – a large networking and SD-WAN vendor – began offering a SASE service. This started with a large base of network features due to its legacy as a networking company.
But, speaking to Versa in January 2021, it said its security features were proving successful. Its solutions like firewalls and ZTNA gaining accreditations and positive reviews after launch.
This demonstrates that while the legacy of the company is important, it is not the only factor.
Companies on both sides of the security and network divide have been growing their capabilities on the other side.
Cavell has seen all approaches to achieve this from in-house development to partnerships.
There have also been many notable acquisitions in this market.
For example, Palo Alto Networks – a leading security company – acquired CloudGenix in April 2021 to gain networking technology and skills.
What is SASE architecture?
Secure Access Service Edge (SASE) is a type of network architecture combining edge security and networking capabilities with cloud-native security functions.
Its purpose is secure management of the web of distributed devices, employees, and sites that now form a business network.
Building this sort of cross-sector architecture presents a challenge to businesses. Many of whom would have had different teams handling security and networking.
But, if each of these teams continues to operate alone, there will be deployment and management problems.
The true gains from SASE cannot come while security and network fall under separate teams within a business.
For businesses that want to adopt a SASE architecture, they must decide on a new internal structure as part of the process.
What is SASE framework?
Secure Access Service Edge (SASE) is a security framework focused on enabling users anywhere to access cloud services in a secure manner.
The goal of the framework is to build a system that can determine risks and deploy solutions if possible, to enable access.
SASE focuses on identity for verification. It begins by confirming the identity of the user and their right to access services. It then deploys security solutions as needed to protect them.
Many SASE solutions also review where the user is, what network they are on, and what they are trying to access.
In this case, a user with appropriate access rights to a cloud service will not be able to access them if the SASE platform cannot secure the network.
How does SASE secure access?
Secure Access Service Edge (SASE) operates on a user-by-user basis to determine the best approach and level of access for each user as they try and access services on the network.
This is based on four steps:
1. Who is the person connecting to the network?
a. What access rights do they have?
b. Are they who they say they are?
c. What device are they using? Is it registered with the company?
2. Context
a. Where are they accessing from? Is it a regular location for them?
b. What network are they using? Is it secure?
c. Is the device they are using infected with a virus?
d. How sensitive are the services they are accessing?
3. Policies
a. How should traffic be managed?
b. Are there limits set on this application?
c. Are there any regulatory requirements?
4. Ongoing risk assessment
a. All of the above monitored on an ongoing basis to maintain ongoing security
What does Gartner say about SASE?
The Gartner report on SASE explains how the old model of business networking – that placed the enterprise data centre at the heart of the network – was not capable of meeting the needs of the distributed business workforce.
The report states:
“By 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.”
This shows this is not just a new area of technology but one that will see considerable growth in the future.
Gartner’s vision is that there has been a change of usage patterns across the business away from centralised to edge computing.
The only way to handle this change in a way that maintains business productivity is to build a new type of security and network architecture where the cloud hosts and manages all these functions.
This cloud-based network fabric will use all the developments made in building flexible software-defined solutions to tailor each instance of a service to the user’s needs.
In doing this, you create reactive architecture that brings solutions as close to the user as possible, making access smoother and more secure.
Cavell agrees with Gartner that this represents an inflection point in these technologies.
It seems that the demands of businesses are no longer served by the way networking security has worked before.
Gartner has aptly (and catchily) named a trend that has been developing in the marketplace for some years.
The origins of this trend lie in how SD-WAN vendors have integrated with vendors offering cloud-based security like Palo Alto Networks or Zscaler.
The truth is that it makes no sense to build large complex on-site data centres to host solutions and manage security if that is not where the employees are.
If the majority of employees are accessing services remotely then the services should also be hosted remotely.
To do anything else is to deny the reality and provide a worse service.
SASE Vendors
Below, you’ll find a detailed overview of the major SASE vendors.
Barracuda Networks
Its sales proposition focuses on this, referencing customers using the solution to enhance Microsoft 365.
It also emphasises its connection to the Microsoft global backbone network for site-to-site and site-to-cloud connectivity.
Cato Networks
Cato Networks is a SASE company with that as its only product. It is one of the youngest SASE companies, been founded in 2015, which has its pros and cons.
Pros
It does not come to the table with as much legacy hardware deployed, or customer base in need of migration to new technologies.
This avoids many pitfalls older companies launching SASE have as they need to build systems that can incorporate legacy customers.
Cons
Cato is less compatible with legacy technology deployments. It requires its own hardware for the service to operate in most instances.
This means that customers must switch fully to Cato rather than upgrading what they already have or using it as a modular upgrade to their current deployment.
For larger companies, with complex legacy networks, this can be appealing but for others it is daunting instead.
Still, the future looks bright for Cato as more companies do want this new technology – and they want it in a clean and well-developed way.
Cisco Systems
Cisco is well-known as one of the networking industry giants. It has provided networking, telephone systems, and telecoms equipment globally since 1984.
Cisco’s SASE product falls under the Cisco Umbrella security solution. It is closely tied to its two SD-WAN platforms: Cisco SD-WAN (Formerly Viptela) and Cisco Meraki.
Cisco has acquired companies like Banzai Cloud, Portshift, and ThousandEyes. These acquisitions bring new security capabilities to be integrated into Umbrella or the SASE product.
With Cisco’s existing market position and strong existing customer base, they are a strong player to watch in the SASE space.
Cisco also has a strong incentive to remain competitive in this space.
SASE, and security companies offering network services, encroaches on its network business.
Cisco must be aware of the competitive threats and advantages from offering SASE.
Cloudflare
Cloudflare, established in 2009, is a US-based web infrastructure and security company.
It launched its SASE platform in late 2020.
The platform combines Cloudflare’s existing Zero-Trust Network Access (ZTNA), Secure Web Gateway (SWG), next-generation firewall, and remote browser isolation products.
The product addresses the security risks that came along with the new model of public cloud and distributed workforces.
Forcepoint
Forcepoint (formerly Websense) founded in 1994, is a security company with a broad product base.
Forcepoint’s SASE product is called Dynamic Edge Protection (DEP). DEP provides an all-in-one approach to web, network, and application security as a service.
This cloud service weaves together all Forcepoint’s security products such as firewalls, intrusion prevention, malware scanning, and URL filtering.
Fortinet
Fortinet, founded in 2000, is a US-based cybersecurity company traditionally focused on hardware-solutions.
Fortinet’s FortiSASE product brings the power of the FortiOS and the Fortinet Security Fabric to any enterprise location.
FortiSASE orchestrates the cloud-delivered services of NGFW, Web Security, IPS, DNS, and Sandboxing to meet the needs of SASE.
Fortinet has shown itself to be a strong entrant in the networking space. It has attracted many customers that see the benefits of implementing these together.
Fortinet also offers a wide price range of solutions that makes its product package appealing. Many of these are also available in a modular deployment so adding new services is easier.
Masergy Communications
Masergy, founded in 2000, is a software-defined networking services company.
Masergy differs from other SASE creators as it focuses on its own managed services, and selling itself rather than relying on a huge partner organisation.
Besides, its SASE/SDWAN managed service, Masergy also provides services like Unified Communications, Cloud Contact Centre and Managed Security.
Customers expect managed service providers to be able to provide a converged and integrated service. These extra services are a natural upsell for any SASE provider offering its own managed service.
McAfee
McAfee Corporation, founded in 1987, is one of the most well-known cybersecurity brands in the world. This is both in the consumer and enterprise markets.
McAfee offering SASE products is a natural step for a security company that is trying to offer flexible solutions. Its customers are asking for support in securing the distributed work force.
But it seems that McAfee, at this point, is providing security products that integrate into SASE rather than its own full-SASE product.
Announced in February 2020, McAfee’s ‘Unified Cloud Edge’ offers Cloud DLP and Threat Prevention, Device DLP, and Web DLP and Threat Prevention.
As of February 2021, McAfee does not offer any of the networking services that would allow it to build its own full-SASE solution.
Given the strengths of the company, Cavell expects it to continue to focus on making its security expertise available through integration rather than offer its own complete SASE solution.
Netskope
Netskope, founded in 2012, is a cloud-native security company. This means that its solutions are cloud-hosted and designed to secure other cloud-hosted solutions.
Netskope focuses on Cloud Access Security Brokers (CASB) and Secure Web Gateways (SWG).
One of the primary reasons for these areas of focus is that they are among the technologies best deployed in the cloud, and vital for cloud security.
Both of these are deployable in a Software-as-a-Service (SaaS) model to corporate and cloud datacentres.
Netskope opts out of the networking side of SASE by focusing on integration rather than networking.
This is a sensible strategy for the company, as it lets it play to its strengths. But, the competitive threat from networking companies offering security is growing.
Perimeter 81
Perimeter 81, founded in 2018, as a VPN company, expanded to offer a converged networking and security cloud-based service.
Perimeter 81’s marketing messaging focuses on the idea of replacing legacy hardware with newer and easier to use options.
This offers many benefits from efficiency and management gains. But many companies will find it hard to shift out legacy assets as the cost can be high.
Palo Alto Networks
Palo Alto Networks, founded in 2005, has grown to be one of the premier security and cloud security companies.
In the early days of SD-WAN, many companies turned to Palo Alto for security integration.
Many companies still use Palo Alto integrations for customers seeking best-in-breed security integrated with SD-WAN.
Palo Alto Networks acquired CloudGenix, a leading SD-WAN provider, in April 2020. This brought a broad SD-WAN and network skills portfolio to the security company.
As of 2021, Palo Alto Networks is working to tie CloudGenix into its ‘Prisma Access’ solution. The goal of this is to create the most comprehensive SASE product of its kind.
In Cavell’s opinion, the company makes a reasonable claim to at least share that title.
While Palo Alto alone lacked the networking tools to claim this, if it integrates CloudGenix it will have a solid networking and security tool.
In 2021, Palo Alto continues to create new integrations between existing solutions and acquisitions.
A major focus of this work is to build integrations between Prisma Access – its Cortex Data Lake. This project will make the security data analysis of Cortex available to the SASE solution.
Versa
Versa Networks, founded in 2012, is a software-based network solutions company.
Versa was one of the early entrants into the SD-WAN market, with a product aimed at Telecoms providers.
Due to this maturity of solution, Versa saw an opportunity to transition from SD-WAN to SASE before the naming of the new trend.
Versa has been working on a SASE solution since before the trend gained its name.
It saw a need for lower latency, increased security, and centralised management, and began designing for this.
Its service offers many deployment models including mixed levels of on-premises and software-only deployments.
It also has a multi-tier platform for lean-IT deployment called Versa Titan for smaller deployments.
Versa has made it possible for all its OS devices to be updated to run SASE.
It does not have any legacy hardware deployed due to the age of the company that it needs to replace.
The system also takes existing technology into consideration. As long as there is a device is in place that can run the Versa OS, then older devices are manageable.
This means that SASE operates in more use cases than some companies that have not planned for backwards compatibility.
Versa has focused its development on a process called single-pass parallel processing architecture.
This is a system where, rather than every security solution decrypting and analysing each connection itself, this happens once with many processes running in a parallel manner.
This process reduces latency caused by security solutions as an important part of optimising security and latency.
VMware
VMware, founded in 1998, is one of the traditional titans of the virtual computing architecture, as it was one of the first companies to successfully virtualise the x86 architecture.
VMware offers large amounts of compute, network, and datacentre services, and has a large global network.
VMware focuses on how to make access to its virtualised services more direct, efficient and better managed. This is one of the main reasons it went into the SD-WAN market when that technology began to develop.
SASE is the next logical step as all these services also need security.
VMware’s approach to SASE is to build it into all its SD-WAN gateways ensuring that the service is available across its network.
These gateways are already deployed across the world meaning that expanding SASE into them makes the service available for all existing VMware customers.
In addition to its own security products, VMware has also focused on a tight integration to Zscaler (seen as one of the leaders in the SASE space).
This partnership means that customers can choose between VMware’s security or Zscalers with a similar user-experience for either.
VMware has seen large success with its SDWAN solution. It is reasonable to expect that its SASE solution will also see success with customers looking for a single integrated solution.
Zscaler
Zscaler, founded in 2007, with the goal of creating a cloud-based security as a service platform.
It has achieved broad success in this space and was recognised for its technology by Gartner and other industry analysts.
It offers cloud-based solutions for Secure Web Gateways, Advanced Threat Protection, Firewalls, Data Loss Prevention, Traffic Shaping, and Threat intelligence.
It does not rely on on-premises hardware making it attractive to businesses in an age of distributed workforces.
Since the advent of SDWAN, Zscaler has been one the primary partners for integration with SDWAN companies like VMware, Silver Peak and more.
Due to its focus on the cloud from early in the company’s history, Zscaler claims to have been “SASE before SASE existed”, though there are several companies making similar claims.
Zscaler’s focus on the cloud has paid off as companies continue to grow more distributed.
This trend will only continue allowing the company to gain further traction with its broad suite of cloud-ready solutions.
Conclusion
SASE is a catchy name for the future of the industry.
But, vendors says they were developing towards a SASE model even before the name.
SASE makes sense for where networks are now, growing more diffuse while also growing more complex every year.
Individual employees need robust security to protect them as they use more and more applications.
This security needs to follow them as they travel and work from home as well as the office.
You cannot have network security changing on that user every time they shift location, potentially many times a week.
There is no reason to endure latency of access requests first routing to a central data centre at your corporate HQ, only to go back out to a cloud data centre to access the solution.
This step makes no sense when you consider how we are now building, managing and hosting our applications and solutions.
How to choose the right SASE provider
So now you know enough about each SASE provider to perhaps trim down your longlist to a slightly shorter version.
Remember, you can only learn so much from high-level overviews. The ideal solution would be a comparison tool that you could plumb in your data and get results like comparing car insurance.
Sounds too good to be true…but it isn’t!
Visit Cloud Networking Experts to compare SASE providers here.
If you need more information on SASE than this overview, explore the State of SASE Networking: 2021 Report on SASE and how networking vendors are adapting to the change.
Share this post
Finbarr Goode Begley
Finbarr is Cavell’s CX/CCaaS and Enterprise Analyst. Finbarr started his career as an analyst with a networking and security focus but moved into CX when he realised how fascinating the space was. Finbarr covers all the topics in CX/CCaaS for Cavell, from service provider strategy to market forecasting and growth. He is also responsible for managing Cavell’s Enterprise research and surveying and regularly manages research projects for customers as well. Prior to working at Cavell, Finbarr was an Account Director at a London-based B2B Tech Public Relations company. Though, he always said that it just didn’t go deep enough into the technology for his tastes.
